Today, the Secret Service announced they foiled some big national security threat. Major news organizations (e.g. NYTimes) have repeated their claims without questioning them.
The story is bogus.
What they discovered was just normal criminal enterprise, banks of thousands of cell “phones” (sic) used to send spam or forward international calls using local phone numbers. Technically, it may even be legitimate enterprise, being simply a gateway between a legitimate VoIP provider and the mobile phone network.
The backstory is a Secret Service investigation into threats sent to politicians via SMS messages. The miscreant used one of this spam farms to mask their origin. When the Secret Service traced back the messages, using radio “triangulation” (sic) to find the mobile phones, they found these SIM farms instead.
One of the reasons we know this story is bogus is because of the New York Times story which cites anonymous officials, “speaking on the condition of anonymity to discuss an ongoing investigation”. That’s not a thing, that’s not a valid reason to grant anonymity under normal journalistic principles. It’s the “Washington Game” of “official leaks”, disseminating propaganda without being held accountable.
The Secret Service is lying to the press. They know it’s just a normal criminal SIM farm and are hyping it into some sort of national security or espionage threat. We know this because they are using the correct technical terms that demonstrate their understanding of typical SIM farm crimes. The claim that they will likely find other such SIM farms in other cities likewise shows they understand this is a normal criminal activity and not any special national security threat.
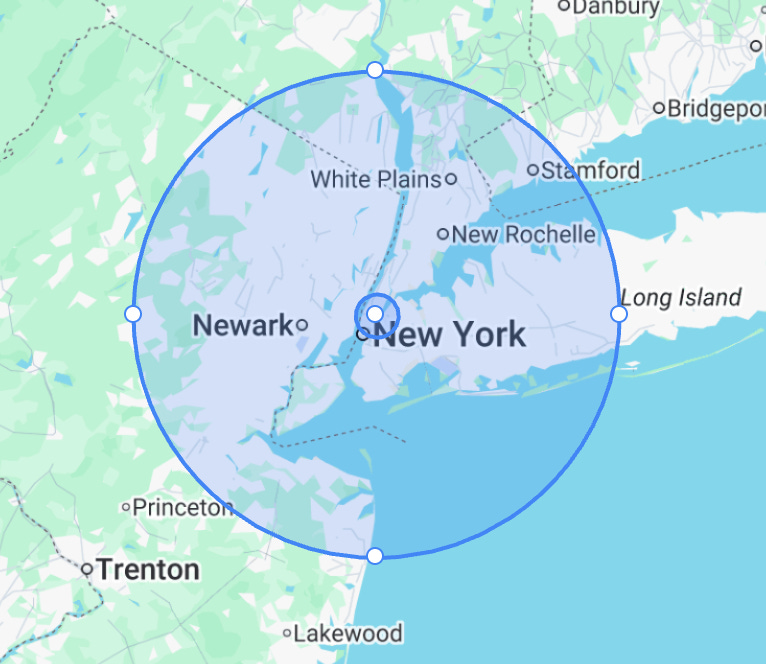
Their official statements are obvious distortions, like being within 35 miles of the UN building. Their unofficial statements are designed to exaggerate even more, like “never before seen such an extensive operation”. The Secret Service doesn’t normally investigate such crime, so of course they are unlikely to have seen such an extensive operation.
Another way you know that the NYTimes is lying is because of the independent “experts” they quote to confirm it.
For decades now, when the NYTimes has a cybersecurity story from anonymous government officials, they quote James A. Lewis to confirm it. This guy used to work for CSIS (Center for Strategic and International Studies) but apparently has changed employers recently. Whenever I blog/tweet about bogus NYTimes cybersecurity stories, I point out this relationship with James Lewis. When you see anonymous government officials and James Lewis quoted in a NYTimes story, you are seeing government propaganda.
Another “expert” the NYTimes quotes is Anthony Ferrante [update]. He’s got the resume that the NYTimes loves. I’m famous among hackers for my technical expertise, but I would never be quoted in the NYTimes, because I don’t matter. The NYTimes only quotes people who matter, meaning, people involved at high levels of government, people with their resume posted on WEF.
Both of these “experts” claim things that are objectively silly. Ferrante says “my instinct is this is espionage” and “c_ould be used for eavesdropping_”. This is false, this arrangement cannot be used for eavesdropping and there’s nothing particularly related to espionage here. Lewis claims “only a handful of countries could pull off such an operation, including Russia, China and Israel”. That’s false, I can pull this off, personally. It’s just a SIM farm. Sure, there’s some capital involved, on the order of $1 million, but it could be setup and managed by a single person. It likely wasn’t setup all at once with that much money, but has been slowly growing for years as profits are funneled back into setting up more SIM accounts
Who are you going to trust, these Washington insiders, “people who matter”, or an actual hacker like myself?
I say “phones” above in quotes above because the actual hardware isn’t like the phones you have in your pocket. Your Android/iPhone is a computer with a single “baseband” radio that talks to the cell tower, and maybe two SIMs in case you have two different phone accounts. That’s what a SIM is — a chip that locks you to a specific phone account.
A “SIM box” has single computer (often running Linux), maybe 20 baseband radios, and maybe 100 physical SIM cards. It rotates among the SIM accounts when spamming SMS messages.
A SIM card may be the same sort of prepaid $10/month SIM you buy at Walmart that allows 1000 SMS messages per month. There are other types of accounts they might use, so they aren’t necessarily walking out of a Walmart with bags full of prepaid SIMs after clearing off the shelves, but it’s close enough. They are trying to fly under the radar, appearing to the mobile networks as normal users.
The Secret Service hypes this as some sort of national security threat that can crash cell towers. The reality is that this is just a normal criminal threat that sometimes crashes cell towers. SMS is an ancient technology that works slowly even in modern cell networks. Too many SIM boxes spamming SMS in one location can indeed overwhelm a cell tower. You actually don’t need a bunch of SIM boxes to do it — you can sometimes crash a cell tower with a single baseband radio. Ask me how I know.
The point is: while criminals do sometimes crash or overload cell towers, an actual foreign threat can do this much easier than using SIM farms. In any event, there are thousands of cell towers around New York City satisfying 10 million subscribers, so crashing a few won’t make much difference.
The correct quote from any expert is that this looks like a normal criminal SIM farm, that’s used for a wide range of purposes, often SMS spam. They are pretending to be thousands of normal mobile phone users to prevent the mobile phone companies from shutting them down. Some miscreant likely used the service to hide the origin of threats sent as SMS messages to politicians, which is why the Secret Service is involved. Theres no evidence the Secret Service is involved due to some actual national security or espionage threat — that’s just propaganda they are hyping.
35 miles radius centered on UN building:
[
Some comments on this blogpost;
[
No posts